There are two camps when it comes to Skype. The "I love Skype so much I'm going to name my first born child 'Skype'" and the "Blasted 'Skype application' is penetrating my security measures at every turn. Damn you Skype! Damn you to hell!" From the user's perspective, the ease-of-use of Skype and its "just plain works anywhere" capabilities are quite attractive. It is Skype's ability to work on any network, regardless of the types of NAT, proxy, firewall, or intrusion prevention systems that have made Skype one of the fastest growing software applications -- and certainly the fastest growing VoIP software application. It is this same set of characteristics that has made Skype the bane of many corporate network managers. Vocal, even bordering on "rabid" arguments have been made opposing industry efforts to block Skype anywhere, while perhaps more civilized arguments have been made supporting very legitimate and compelling reasons to block Skype.
I am not going to debate the issue of whether or not Skype should be blocked, but at least at the corporate level, in my opinion the corporation should be empowered to control what happens on their network. Blocking Skype at the ISP level (i.e. if MCI blocked all Skype IP traffic) is a whole other argument which I am wholeheartedly opposed to. Update: Just noticed Rich Tehrani posted a related post titled Skype Fear that discusses some of the issues involving Skype and trust.
But at least for the corporate environment, there are legitimate reasons to want to block Skype, which I will explain how to do using one of SonicWALL's firewalls which recently added firmware capable of blocking Skype. First, let me explain why Skype is so hard to block. Skype uses an aggressive adaptive networking application that is designed to reach the Internet at all costs. Skype sessions use an asymmetric key exchange to distribute the 256 bit symmetric key employed by the AES cipher for session encryption. Skype's initial outbound connection can use any dynamic combination of TCP and UDP ports, including outbound ports 80 and 443 which are generally open for HTTP and HTTPS access. This renders traditional port blocking filters completely ineffective. In addition, Skype uses proprietary methods of NAT traversal similar to STUN (Simple Traversal of UDP the NAT), ICE (Interactive Connectivity Establishment) and TURN (Traversal Using Relay NAT) to ensure that you can reach the Internet and to determine the client's eligibility to be a supernode.
You could try and figure out which servers Skype uses, but that's a moving target that will constantly change at Skype's whim and as such is a losing battle for any network administrator. Thus, port blocking and IP address blocking won't work. The only way to effectively block Skype is via a packet inspection firewall that can detect the Skype signature.
There are a few products that do this, including Verso Technologies (at carrier/ISP level),Packeteer (enterprise product), and SonicWALL's enterprise appliances. What's unique about SonicWall's latest firmware is that it goes beyond conventional signature-based intrusion-detection and prevention platforms by employing a detection engine that can distinguish not only individual fingerprints, but sequences of fingerprints. According to SonicWALL, "This ability to recognize disjointed, seemingly unrelated sequences of traffic and to accurately coalesce them into identifiable cohesive units enables SonicWALL's Deep Packet Inspection to reliably and accurately identify and control the most elusive protocols even Skype." In order to have this Skype-blocking capability using SonicWALL, you'll need SonicOS Standard or Enhanced 3.1.0.12 or newer (Skype detection capabilities were introduced in SonicOS 3.1.0.5)
SonicWALL customers with current service/software support contracts can obtain updated versions of SonicOS firmware from the MySonicWALL customer portal at https://www.mysonicwall.com. Updated firmware is also freely available to customers who have registered the SonicWALL UTM appliance on MySonicWALL for the first 90 days.
Interestingly, below are the easy-to-follow steps outlined on SonicWALL's website for blocking Skype:
Before you begin to configure your SonicWALL UTM appliance to block Skype, perform the following steps:
1. Select a workstation on a firewalled segment (e.g. LAN/Trusted, DMZ/Public, WLAN/Wireless) on which Skype is installed, or select a workstation on which to install Skype for testing.
2. Launch the Skype application. Login with an existing account, or create a Skype account and then login.
3. Observe that Skype can successfully connect to the Skype network.
4. Close the Skype application.
Detecting and blocking Skype begins with activating Intrusion Prevention Services (IPS) on the SonicWALL appliance. At the time of this writing (December 2005) the SonicWALL PRO 4100 and PRO 5060 include one-year of complimentary Gateway Anti-Virus, Anti-Spyware and Intrusion Prevention Service. SonicWALL TotalSecure 10, TotalSecure 25 and TotalSecure Enterprise packages (http://www.sonicwall.com/totalsecure/index.html) also include one-year of these services. Other platforms are also eligible - refer to http://www.sonicwall.com/products/gav_ips_spyware.html for details.
Perform the following steps to enable the detection and blocking of Skype:
1. Enable IPS
a. Activate by Interface on SonicOS Standard
b. Activate by Zone on SonicOS Enhanced
2. Enable detection / prevention of the Skype signatures
a. This can be done by individual signature, or at the group (IM) level. This example will activate Skype detection and prevention at the IM Group level.
Enable IPS
1. From the Security Services > Intrusion Prevention page, select the Enable IPS checkbox, and click the Apply button at the top right of the page.
Activate by Interface on SonicOS Standard
a. From the Security Services > Intrusion Prevention page, select the interface(s) on which you wish to enable IPS
b. Click the Apply button.
Activate by Zone on SonicOS Enhanced
a. From the Network > Zones page, select all the zones of which you wish to block Skype. In this example, it is assumed that the workstation under test will be connected to the LAN Zone - select the edit icon for the LAN Zone.
b. Select the Enable IPS checkbox on the General Tab. Click OK.
c. Ensure that IPS is checked in the Zone Settings view:
Enable Detection / Prevention of the Skype Signatures
For ease-of-configuration, IPS Signatures can be enabled on multiple levels:
• By Priority - There are High, Medium, and Low priority groups. Skype is in the Low priority group. Generally, the Low priority group should not configured for "Prevent All" because of the broad range of traffic included in this group, including commonly used diagnostic/reconnaissance traffic such as ICMP.
• By Category - There are currently 41 categories. The Skype signatures are in the IM category. The IM category also includes other well-known IM applications such as AIM, ICQ, MSN, Yahoo, and QQ.
3 • By Signature - There are currently 2,155 signatures, which can inherit settings from the Category or Priority level, or which can be individually configured.
SonicOS Enhanced also provides inclusion/exclusion controls for Users/Groups, IP Addresses (Address Objects) and Scheduling controls. Refer to the IPS Primer (SonicWALL_IPS_First_Primer.pdf) for more information on these controls.
In this example, we will be enabling Skype detection and prevention at the Category level:
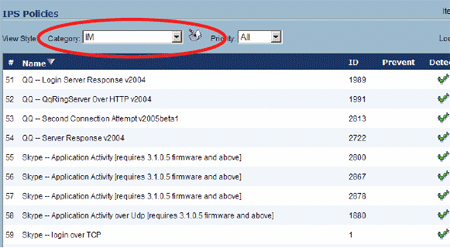
1. From the Security Services > Intrusion Prevention page, select the IM category from the Category drop-down. The page view will update. Click the edit icon to the right of the category.
2. The Edit IPS Category window will differ slightly depending on your SonicOS version. Select Enable for Detection and Prevention and click OK:
3. Confirm that Prevent and Detect are checked for the IM signatures in the IPS Policies table.
Testing
Now that Skype detection and prevention is enabled, launch the Skype application on your test workstation, and attempt to connect to Skype. If the Skype application was previously running, refer to the "Caveats" section on page 2.
Skype will fail to connect. You can verify the SonicWALL UTM appliance detection and prevention activity by browsing to the Log > View page:
Conclusion:
There is a lot of interest in the business enterprise to block Skype. I'm sure I've probably "rankled a few feathers" by bringing to light some products that enable you to block the Skype application, but as much as Skype has become a religion to some, it is still just another software application that network administrators have every right to govern, monitor, and block. I wouldn't be surprised if Linksys, D-Link, Netgear, or the other SOHO firewall players decide to add more powerful IPS capabilities that can block Skype or even apply QoS policies. Many of them already have rudimentary intrusion detection but can't block Skype. Of course it would behoove Cisco to offer the ability to apply individual and group policies that let some enterprise users use Skype (CEO, VPs, etc.) while blocking it for those that don't need it, as well as setting a QoS metric to the Skype packets.
Source








No comments:
Post a Comment